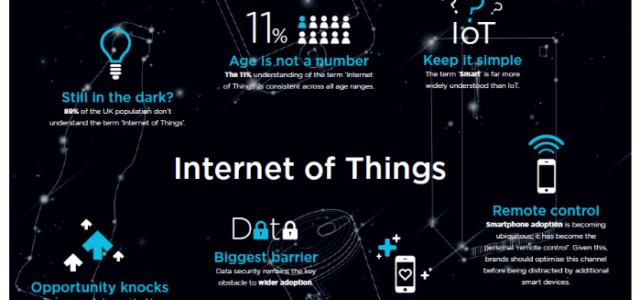
I’m struggling to think of another profession where ‘things’ is a suitable description of a product, service or problem. Everything from a light bulb and a fridge to a car or a plane is now a ‘thing’. Because we haven’t been vague enough already, we throw into the Internet of Things (IoT) quagmire some real esotericism in the form of Machine Learning and Artificial Intelligence to deliver Smart solutions. I’m confused. Is IoT really an entirely new set of technologies?
Industry rhetoric suggests a ‘sophistication of attack’, whenever the latest botnet commandeers thousands of ‘things’, but I’m not so sure what is sophisticated about hunting for default creds on a collection of cameras. The same occurs when we look at Industrial Control Systems (ICS). The media suggested that the world was on the verge of an apocalyptic catastrophe through with the headline, Hackers gaining direct access to the power grid! I am not suggesting we avoid a discussion around the impact of risks on critical infrastructure, but mitigating controls should always be considered. In the power grid scenario, hackers might be successful in taking an individual station offline but a successful attack on a distributed, complex and resilient energy ecosystem is a far more unlikely proposition.
In the same way that technology has driven cultural demand for instantaneous service and frictionless security, internet connectivity is now almost a mandatory capability. If that’s the case, surely, it’s prudent to find a better delineator than the fact that something has an IP address. When does a computer cross the divide into being a thing, or vice versa?
In the early ‘noughties’, the thought of allowing own device access to corporate applications was unheard of, but in 2017 the concept is ubiquitous. The idea of 20billion IoT devices by 2020, if reports are to be believed, certainly brings problems, but the issues very rarely emanate from proprietary or unique technology challenges; they stem from a handful of intrinsically linked issues.
Six key issues of IoT
The Hardware Industry Needs Motivation.
When it comes to secure development and patching, hardware vendors are at least a decade behind the software industry. At the turn of the millennium, software vendors were forced to rethink their approach to security and ensure that it was built into their products throughout the development lifecycle. This principle grew into the ‘move security left‘ paradigm which is thankfully growing in prevalence across our industry and into cross-functional, DevOps teams. Developers were forced to make this change because vulnerabilities were being discovered in shoddy software products. Poor security meant that consumers would buy something else.
In light of ‘IoT-pwnage’ over the past 12 months, hardware manufacturers will need to up their game. Unlike vulnerabilities in software, which can be addressed with a simple patch, many hardware products today have no easy means of patching the firmware. As such, an entire generation of hardware devices will simply need to be replaced when critical vulnerabilities are uncovered. Easy for a light-bulb, slightly harder for a plane.
While manufacturers are under enormous pressure to be the first to market with the latest IoT devices, the problem of security is broadly surmountable. A lot can be achieved through education. Selling devices with predictable default configurations and poor password management is simple to fix and inexpensive. If security becomes a consumer requirement, hardware vendors will need to ensure a baseline level of protection. Yes, margins might drop in the short term but it’s the same for everyone.
It’s Tough Finding Vulnerabilities
The organisational attack surface continues to expand and the more device types and form factors that we must deal with, the tougher it is to have any semblance of enterprise visibility. When was the last time you penetration tested your photocopier or HVAC system, yet both are now likely to be connected? CISOs need to adapt and take a broader view of the assets that they are tasked with protecting.
A significant challenge when securing IoT devices comes from the fact that organisations simply don’t know where they are. Today, an employee can quite easily purchase a webcam, connect it to a guest Wi-Fi network and monitor his office remotely. As we learned recently thanks to the Mirai botnet, these IoT devices are network connected computers and can be remotely repurposed by a botnet. Even if the devices have limited internal access, they can in the case of the Dyn attacks be leveraged as powerful weapons in a DDoS attack.
Automation and Downstream Risk
There is no doubt that IoT-enabled devices provide consumer convenience but they also increase the need for holistic risk management and threat modelling. Let’s take digital assistants such as Amazon Echo, Google Home and others, for example. In isolation, their threat profile is innocuous enough, but their main benefit is also their vulnerability: extensibility and integration.
These devices become exponentially more useful, the greater the number of manual, multi-phased tasks they can perform. So, what happens if one of these devices is compromised? The home assistant has become the contemporary ‘Doman Admin’. Why go through the effort to compromise a laptop, when you can grab the keys to the kingdom via a straightforward appliance rooting. With orchestration – be it a home assistant or an Enterprise Cyber SOA platform – we are aggregating control to a single source of truth. This feels diametrically opposite to the distributed ledger approach being used with blockchain-based technologies.
But there’s more. What about the data leakage and privacy? The default options for most smartwatches send a plethora of personal information to the cloud. As a non-technical consumer, this shipping of my heart rate, weight, dietary requirements and exercise routine feels implicit but the embedding of ‘consent’ in a 25-page EULA isn’t going to be a permissible defence come 25th May 2018.
Machine Learning is not a Silver Bullet
Simply put: garbage in, garbage out. Machine learning (ML) gives immense power to businesses by adding power and automation to previously time-consuming, resource-intensive activities. ML is used to identify malware, predict stock prices, tailor an investment portfolio and drive a car. In an IoT capacity, ML is best evidenced through smart devices. But machine learning doesn’t work well on all problems. In cases where the pattern is new or where there isn’t enough data available, a machine learning model will not fare so well. While there are techniques available to support a wide variety of use cases, there remains a need for human validation, sense-checking and domain knowledge. The biggest challenge for self-driving cars is being able to react to the randomness of traffic flow and other drivers.
The ‘CIA Triad’ Needs a Rethink
From CISSP exam study we learn that ‘all risks are associated with confidentiality, integrity and/or integrity’. It’s a mantra I’ve been using for years but the IoT changes all of this. It’s now: CIAS where the ‘s’ is ‘safety’. Until recently, and with very few exceptions, information security programmes and standards focused on risks associated with data. If you’re now looking at a thing, the goalposts have moved.
CIA works well for situations where data processing is the primary objective. The primary purpose of a laptop is the processing of ones and zeros to write an article, order a take-away or watch cat videos, for example. A thing has a different, primary, purpose, from keeping my food cold to flying at 40,000 feet. The number one business priority for an airline is the safety of their passengers.
A traditional risk equation looks like this: Likelihood x Impact = Risk. With many of our things this equation now becomes a matter of life or death.
Trying to fix the security of all IoT devices just isn’t going to work. In the same way that your volumetric DDoS protection service is critically important for internet facing e-commerce channels, it’s a waste of money and totally ineffective to sit in front of a development website in your innovation lab.
CISO: “OT is not my Problem”
Operational Technology (OT) is a term to describe the hardware and software used to monitor the running of physical devices. Things like pumps, valves, sensors, etc. The issue as we come into 2018 is that these systems can also leverage the inherent benefits of network connectivity.
Not worrying about antiquated industrial control systems and their vulnerabilities was okay when these systems were truly ‘air-gapped’ but this is no longer the case. Reports suggest that a third of all industrial sites are connected to the internet. Surely, if we pop an OT system, which controls a dam, an electrical grid or a nuclear enrichment facility, then the consequences are exacerbated. I appreciate that rhetoric isn’t always helpful but along with impact, other problems reside in the OT world which are intrinsically linked.
But where is the ownership of OT? Historically, OT systems haven’t sat under the CISO. Why? Firstly, they were not connected to the internet or considered IT systems and secondly, the CISO reported to the CIO and OT wasn’t a land grab worth pursuing.
Article by channel:
Everything you need to know about Digital Transformation
The best articles, news and events direct to your inbox
Read more articles tagged: Featured, Internet of Things