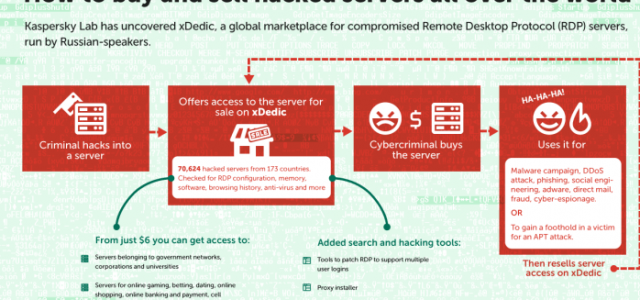
Transformation of Cyber attacks to APT-as-a-service has begun
Hackers as a next big move have started hacking critical servers of business organizations, taking…
thedigitaltransformationpeople.com


Hackers as a next big move have started hacking critical servers of business organizations, taking…
thedigitaltransformationpeople.com

Everyone’s life in today’s world starts with the use of e-mails. The fact is that…
thedigitaltransformationpeople.com

In the latest GDS Video Snack, Sasha Qadri, Editor at MeetTheBoss TV looks at how…
thedigitaltransformationpeople.com

Barely a day goes by when you don’t read in the papers about some security…
thedigitaltransformationpeople.com

Power corrupts and absolute power corrupts absolutely.~ Lord Acton Over a year ago a colossal…
thedigitaltransformationpeople.com

If the Internet is a free-for-all, and with the Internet of Things we’re putting the…
thedigitaltransformationpeople.com

As someone who has been directly involved in cyber security training for the last decade,…
thedigitaltransformationpeople.com

It has been identified by the security researchers that an SQL injection might have been…
thedigitaltransformationpeople.com
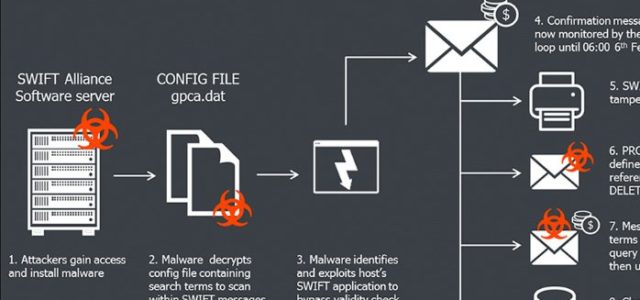
Finally by now the puzzle behind the Eighty Million USD Bangladesh Central Bank hack attempt,…
thedigitaltransformationpeople.com
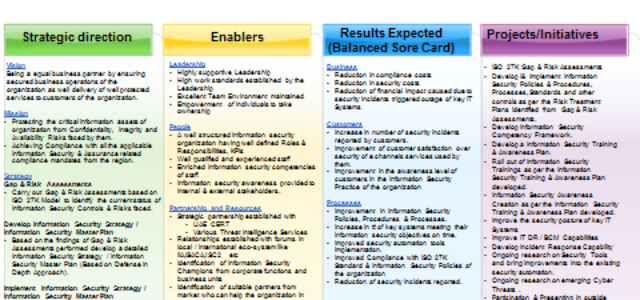
Why Information Security requires strategic planning? Strategic planning is the process that supports an organization…
thedigitaltransformationpeople.com

I am sure all of you have heard about the biggest data leak in the…
thedigitaltransformationpeople.com