Finally by now the puzzle behind the Eighty Million USD Bangladesh Central Bank hack attempt, has been solved.
How this hack attempt was executed: Investigators from British defense contractor BAE Systems have done an exhaustive investigation of the Bangladesh Bank hack attempt and have discovered that hackers who have stolen $81 million from the Bangladesh Central Bank has successfully hacked the SWIFT platform of the Bank for executing these illicit transactions.
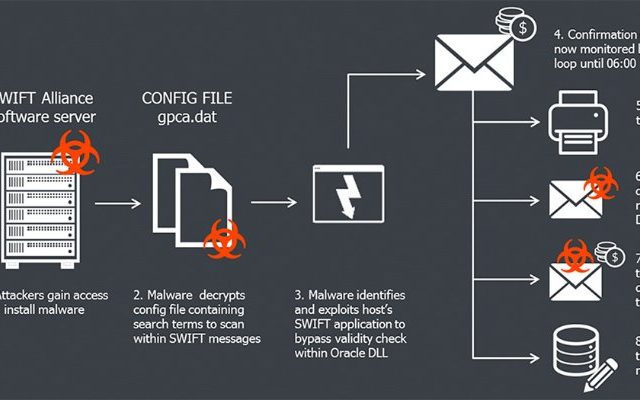
The investigators have found a “custom malware” developed by an individual based in Bangladesh, which contains sophisticated functionality for interacting with local SWIFT Alliance Access software running in the infrastructure of Bangladesh Central Bank. The BAE researchers have identified that as a first step the malware has targeted Alliance Access, a piece of software that allows banks to connect to the SWIFT network. This was executed by compromising the very poor quality network switches connecting computers to SWIFT Network. Amazingly no firewalls were found to be in place in the Bank dealing with such high volume money transactions.
First they hacked the swift alliance software and got access into SWIFT server. Than they have executed the fraudulent money transfers. Than the malware they have used has erased records of illicit money transfers done with the help of compromised SWIFT system. This malware was designed not just to alter SWIFT transactions, but also to hide their alterations. All money transfers sent by SWIFT’s software will be sent to a printer. If the fraudulent transaction confirmations are printed out, the banking officials can spot an anomaly and then respond appropriately to stop such transactions from happening. Hence, the malware used by the hackers also intercepted and tampered the SWIFT transfer confirmation messages sent to printer and then sent the tampered copies of such messages in order to cover up the fraudulent transactions.
The malware was able to be installed on the SWIFT software computer because the traces(logs) of attacker was found to be into Bangladesh Bank’s network presumably with enough access to override any locally installed security software if there was any. So the investigators doubt the involvement of an insider connection also into this hack attempt. What they is hackers can successfully access many systems without insider assistance. But they certainly need insider support to have the knowledge of fraud detection controls in place, which could have only come from a current employee at SWIFT or Bangladesh Bank.
Swift has also made an statement stating that this malware was designed to hide the traces of fraudulent payments from customers local database applications and could have been installed on users local systems by attackers that have successfully identified and exploited weaknesses in their local information security arrangements.
Critical takeaways for us from this incident:
- We should conduct SWIFT transactions only on computers that are isolated from other devices in the network. It should be a dedicated computer
- We should ensure the adequacy of the existing network security & malware protection controls
- We should perform periodic application security reviews around critical systems exist in place such as SWIFT
- We should perform periodic database security reviews
- Every six months we should do a COMPROMISED assessment to see potential compromises into our IT Infrastructure
- We should develop an Incident Response Capability supported with policies, procedures, SIEM and Security Analytics Tools
- We should ensure the ongoing information security awareness among staff, vendors, partners with whom we work with.
Article by channel:
Everything you need to know about Digital Transformation
The best articles, news and events direct to your inbox