Why Information Security requires strategic planning? Strategic planning is the process that supports an organization in setting up goals and objectives towards achieving some desired destination in Business.
Strategic planning also helps an organization in identifying the various resources required for achieving the goals and objectives identified.
An Information Security Strategy and Master Plan will help an organization in identifying and mitigating the various risks faced by the variety of information assets owned by organization and ensuring the Confidentiality, Integrity and Availability of information assets.
Also Information Security Strategy will help an organization in bringing in improvements into the Information & Cyber Security Practices of an Organization. An effective information security strategy & master plan is need of the hour for managing the broad spectrum of cyber security threats emerging globally.
Inputs for Information Security Strategy & Plan Development
Development of Information Security Strategy need to consider various inputs arising from
Stakeholder Requirements Analysis
- Information Security Risk Assessments
- Bench marking with Industry
Stakeholder Requirements Analysis:
Inputs from the following list of stakeholders need to be considered and analyzed for the development of Information Security Strategy & Master Plan:
- Customers
- Business Unit Heads
- Staff
- Executive Management Team
- Board of Directors
- Audit Committee
- Business partners
- Investors / Shareholders
- Vendors
- Service Providers
- Local Authorities (Such as Police, Civil Defense, Fire Brigade)
- Regulators
Information Security Risk Assessments
Conducting information security risk assessment is one of the critical pre cursor activities for information security strategy development.
Information Security Risk Assessments can be performed in the basis of information security risks faced by
- Critical Information Assets
- Critical Business Processes
- Critical Technology Infrastructure
- Critical IT Applications & Business Systems
- Critical People Resources
- Critical Information Processing Facilities (Data Centers, Disaster Recovery Site etc).
Risk Assessments will have the following set of activities:
Risk Identification
- Risk Analysis & Evaluation
- Risk Mitigation Planning
Organizations can practice the following options as Risk Response:
Accept the Risk
- Avoid the Risk
- Transfer the Risk
- Mitigate the Risk
Risk response will be decided based on the rating of residual risks and the risk appetite/ risk acceptance criteria of the organization.
The following frameworks can be used for conducting information security risk assessment:
ISO/IEC 27002:2005
- ISO/IEC 27005:2011
- OCTAVE
- CRAMM
- FAIR
- RISK IT
- MEHARI
- MAGERIT
- EBIOS
- CORAS
- COBRA
- IT-Grundschutz
- FRAP
- ISRAM
Benchmarking with Industry
In a periodic basis the information security management practices of the organization needs to be benchmarked with peers in industry to identify potential improvement opportunities in the information security management practices of the organization.
Also benchmarking the information security management practices such as COBIT, ISO 27001, ISM3, Security CMMI, BSIMM, OWASP kind of industry best practices also will help in identifying potential improvement opportunities in the information security management practices of the organization, which will be one of the critical inputs towards developing information security strategy of an organization every year.
Components of Information Security Strategy & Master Plan
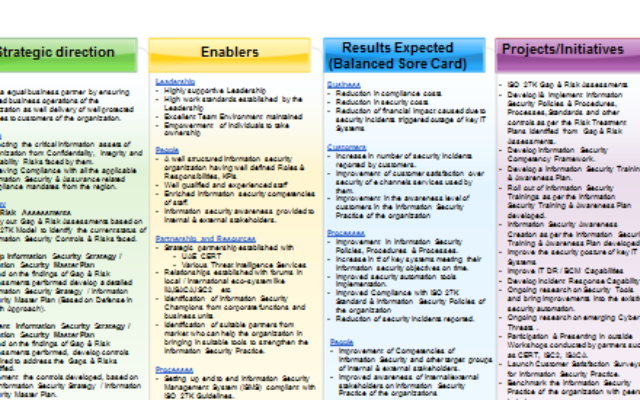
The Information Security Master Plan shall consist of several interconnected components derived from various sources that contribute to the overall Information Security Strategy & Plan of an organization. Vision, Mission, Strategic Objectives, Business Drivers, Enablers, Results Expected, Initiatives are the key components of an Information Security Master Plan.
Once each component has been implemented, the plan will enable an organization in proactively reducing risk, adhering to regulatory, security, and privacy standards, and enabling Information Security to effectively support its business requirements.
Vision
Vision refers to the destination where an organization wants to be in the future. Giving herewith a sample information security vision statement:
Sample Information Security Vision Statement
“Being an equal business partner by ensuring secured business operations of the
Business as well delivery of well protected business services to customers “.
Mission
Mission is the reason for the existence of an organization. Giving herewith a sample information security mission statement:
Sample Information Security Mission Statement
“Protecting the critical information assets of the organization from Confidentiality, Integrity and Availability Risks faced by them “
Strategic Objectives
Strategic Objectives are broadly defined objectives that an organization must achieve to make its strategy to succeed.
Sample Information Security Strategic Objectives
Perform Information Security Gap & Risk Assessments based on Best Practices such as ISO 27OO1
- Develop Information Security Strategy / Information Security Master Plan
- Implement Information Security Strategy /Information Security Master Plan
- Continuous Improvement of Information Security Practice
Business Drivers
Business drivers are critical factors that determine the continued success and sustained growth of a business. The various business drivers for Information Security Management are given below:
- Compliance mandates, legislation, standards and regulations (management controls, privacy, etc)
- Protecting the company’s image and reputation
- Information security requirements of business units
- Protection required from internal and external threats
- Unauthorized access into critical IT Systems
- Loss of intellectual property
- Use of Malicious software
- Business interruption due to IT Systems Outages and unethical hacking
- Business interests in high-risk regions, countries, expanding market segments (e.g., gov’t)
- Extended enterprise models (business partner arrangements, networking requirements)
- Portable computing variations (on-site, remote, wireless)
Enablers
Enablers are the critical capabilities, forces, and resources that contribute to the success of an entity, program, or project. Various enablers of a successful Information Security function are listed here:
Leadership
- Highly supportive Leadership
- High work standards established by the Leadership
- Excellent Team Environment maintained
- Empowerment of individuals to take ownership
People
- A well-structured information security organization having well defined Roles & Responsibilities, KPIs
- Well qualified and experienced staff
- Enriched information security competencies of staff.
- Information security awareness provided to internal & external stakeholders.
Partnership and Resources
- Strategic partnership established with CERT kind of external partners
- Various Threat Intelligence Services
- Relationships established with forums in local / international eco-system like IIA,ISACA,ISC2 etc
- Identification of Information Security Champions from corporate functions
- Identification of suitable partners from market who can help the organization in bringing in suitable tools to strengthen the Information Security Practice of the organization.
Processes
- Setting up end to end Information Security Management System (ISMS) compliant with ISO 270001 Standard Guidelines
- Setting up various Information Security Policies & Procedures, Guidelines, Checklists, Standards and other controls
- Appropriate level of automation of Information Security Policies & Procedures using tools that will help in strengthening the Information Security Practice.(Such as Firewalls, IDS/IPS, SIEM, DLP, Encryption, Mobile Security Tools)
Results Expected
Results expected out of Information Security Master Plan can be derived based on a conventional Balanced Score Card approach which will have 4 quadrants such as customer satisfaction, financial benefits, learning & development planned, internal process improvements. Sample results are listed down below:
Financial Benefits
- Reduction in compliance costs
- Reduction in security costs
- Reduction of financial impact caused due to security incidents triggered outage of key IT Systems
Customer Satisfaction
- Increase in number of security incidents reported by customers.
- Improvement of customer satisfaction over security business services used by them.
- Improvement in the awareness level of customers in the Information Security Practice.
Internal Process Improvements
- Improvement in Information Security Policies, Procedures & Processes.
- Increase in # of key systems meeting their information security objectives on time.
- Improved security automation tools implementation.
- Improved Compliance with ISO 27K Standards & Information Security Policies of the organization.
Learning & Development
- Improvement of Competencies of Information Security and other target groups of internal & external stakeholders.
- Improved awareness of internal/external stakeholders on Information Security Practice.
Projects / Initiatives
These are the list of initiatives identified towards achieving the strategic objectives of Information Security function in an organization. Sample projects/initiatives are listed down below:
- ISO 27K Gap & Risk Assessments
- Develop I& Implement Information Security Policies & Procedures, Processes, Standards and other controls as per the Risk Treatment Plans identified from Gap & Risk Assessments.
- Develop Information Security Competency Framework.
- Develop an Information Security Training & Awareness Plan.
- Roll out of Information Security Trainings as per the Information Security Training & Awareness Plan developed.
- Information Security Awareness Creation as per the Information Security Training & Awareness Plan developed.
- Improve the security posture of key IT Systems
- Improve IT DR / BCM Capabilities
- Develop Incident Response Capability
- Ongoing research on Security Tools and bring improvements into the existing security automation.
- Ongoing research on emerging Cyber Threats.
- Participation & Presenting in outside Workshops conducted by partners such as CERT, ISC2, ISACA.
- Launch Customer Satisfaction Surveys for Information Security Practice.
- Benchmark the Information Security Practice of the organization with peers in industry.
- Periodic VA/PT, Reviews, Audits and Risk Assessments around Information Security Practice.
Re engineer and improve the effectiveness of Information Security Policies & Procedures and the organization wide information security operations.
Putting all the individual components we have seen so far together we will be able to assemble the information Security Master Plan.
Stakeholder Involvement & refreshing of the Information Security Strategy/Plan
After development, Information Security Strategy & Plan needs to be communicated to the above seen stakeholders for having their reviews and suggestions for enhancing the strategy & plans further.
Also in ongoing basis these stakeholders will be appropriately and as required involved in refreshing the information security strategy & plan to meet the dynamically changing business requirements and information security threat landscape. As a minimum Information Security Strategy & Plan needs to get revisited once in a year for refining and retooling purposes.
Major changes into the information security strategy & plan will happen only based on critical business changes and changes from industry and stakeholders.
Defense In Depth Approach for implementing Information Security Strategy
It is advisable that development & implementation of Information Security Strategy of an organization follows Defense In Depth (DID) Mechanism which is a multi layer protection offering approach. Meaning if one layer of security controls fails another layer of controls will come for rescue.
Using a multi layered approach like Defense In Depth Mechanism will help organizations in reducing an attacker’s chance of having success entry into organization’s network and physical perimeters.
Aligning Information Security Strategy with Corporate Business Strategy
Information Security Objectives identified cans be complied into the form of strategy maps and the same will be developed into the form of Information Security Score card. Information Security Scorecard provides a structured approach to evaluating the:
Risk Acceptance Criteria of an organization
- Identifying acceptable risks, and
- Prioritizing the risk mitigation activities.
Having such an Information Security Score Card will help in addressing the alignment of Information Security Objectives with Business Objectives and it will also make the Information Security Strategy much relevant to the information security team and other stakeholders.
Socializing Information Security Strategy & Plan
Communication channels exist within organizations need to be effectively used for socializing Information Security Strategy & Plan wherever possible. Communication channels such as emails, video & audio messages, posters, web casts, web site publishing will be used for adding variety into the communication and to reach out to wider audiences by taking advantage of existing technology communication methods. A detailed communication matrix needs to be developed for briefing on which stakeholders will get communicated on information security strategy & plan by whom and by when.
The following are some of the key communications around information security practices of the organization that should be sent to internal & external stakeholders of the organization in need basis:
Information Security Strategy & Plans of the organization
- Changes happening into the Information Security Strategy & Plans of the organization
- Key Decisions taken by the Management Team around Information Security Management Practice of the organization
- Participation/Sponsorship required from Internal & External Stakeholders for the Information Security Management Practice of the organization
- Newly emerging information security threats outside and organization’s plan to manage the same
- Critical Information Security Breaches & Incidents reported internally
- Launch of new information security awareness and training sessions by the Information Security Team of the organization
- Launch of new projects & initiatives started by Information Security Team of the organization
- Messages received from local authorities and special interest groups around Information Security
- Messages received from regulators in the region on newly introduced legislations around Information Security Practices plan for addressing the same
- Results/observations from internal & external audits, risk assessments conducted around Information Security Management Practice of the organization
- Messages around fire drills, evacuation drills planned/conducted at the organization and its branches
- Business Continuity & Disaster Recovery Plan Arrangements of the organization
- Information Security Management Best Practices of the organization
Conclusion
Organizations should invest adequate amount of time in building a matured and future focused Information Security Master Plan considering the emerging internal threats and external threats. It’s very important that in the process of building the Information Security Master Plan, organizations give equal importance to People, Process and Technology elements.
The Information Security Master Plan should be built as an integrated one comprising of these 3 components which will help an organization in ensuring that the confidentiality, integrity, availability and reliability of its information assets are secured and being resilient and reliable in the vulnerable cyber space around.
Article by channel:
Everything you need to know about Digital Transformation
The best articles, news and events direct to your inbox
Read more articles tagged: Featured