Hackers as a next big move have started hacking critical servers of business organizations, taking full control of them and selling them for cheap on a black market called xDedic. These servers are being sold for a rock bottom prices, like $ 7 J.
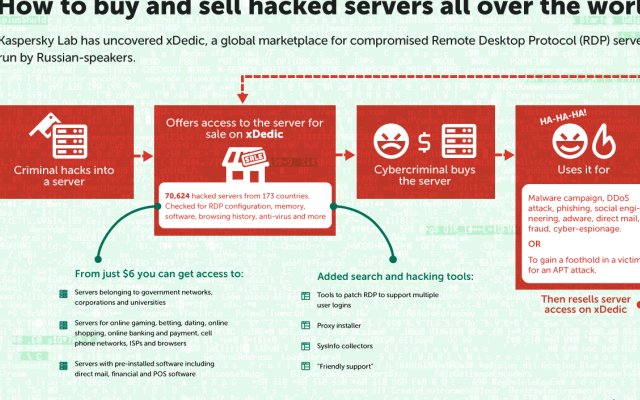
“xDedic” is a trading platform where cybercriminals can purchase any of over 70,000 hacked servers from all around the internet. It appears to be run by a Russian-speaking group of hackers.
From governmental networks to corporations, it is possible to find almost anything on xDedic for as little as 6 USD per server. This one-time cost provides a malicious “customer” with access to all the data on the server and endless other possibilities, such as using the access to launch further attacks.
In March 2016, the sales inventory included access to 51,752 servers from 183 countries, located in 11,050 different subnets. There were 425 unique sellers on the marketplace. As of now this marketplace has listed down 70,624 servers from 416 unique sellers in 173 affected countries for sale. Big names such as Barclays, chase, paypal, suntrust, capitalone, wellsfargo. Western union are being part of this list which is very shocking. The following is the list of servers attacked and kept for sale from banking & payment system related domains: · aib.ie
· barclaycardus.com
· capitalone.com
· chase.com
· chaseonline.chase.com
· coinbase.com
· entropay.com
· liqpay.com
· moneybookers.com
· money.yandex.ru
· open24.ie
· payeer.com
· paypal.com
· paysurfer.com
· perfectmoney.com
· qiwi.com
· suntrust.com
· skrill.com
· webmoney.ru
· wellsfargo.com
· westernunion.com
The list gets widened more by having other industry biggies such as Walmart,UPS, Verizon, Skype and many more.
So server security needs to get ensured to the maximum by taking the following security measures:
· Apply all the latest patches announced by vendors
· Revisit firewall rules, IDS/IPS, end point protection arrangements for addressing gaps (If any)
· Don’t install software that is not used.
· Restrict access to directories with proper permissions
· Make sure logs are working properly.
· Make sure that all admin level accesses are logged with date, times and usernames.
· Remove default accounts in MySQL.
· Secure SSH
· Secure Apache
· Disable direct root login in SSH.
· Get rid of passwords with SSH keys.
· Disable unused services.
· Monitor web traffic for unusual activity.
· Harden default service settings in Apache, SSH and other services.
· Harden /tmp partition
· Lock down system compliers
· Use root account only when required.
· Use private networks for internal server traffic.
· Use encryption when appropriate.
· Ensure the timeliness and appropriateness of server backups
· Enforce strong passwords and change policies for all the server
Indeed cyber attacks such as these attacks have started giving life to the idea of transformation of plain cyber attacks into APT-As-a-Service Model.
Article by channel:
Everything you need to know about Digital Transformation
The best articles, news and events direct to your inbox