Blockchain has captured the imagination of intellectuals and polity alike with economists, technologists, governments raving about its potential and how its poised to fundamentally change the world.
Though the very genesis of blockchain was about disintermediating banking and introducing a transparency that didn’t require numerous layers of intermediaries and central authorities, it’s the financial services that’ve in fact turned out to be one of the first to embrace blockchain. Devising use cases for a range of services from cross border payments, remittances, trade finance to loyalty programmes, the financial services industry has been actively leading the blockchain experiments. And, why shouldn’t it?
Take cross border payments for instance. On average, it takes 3-7 days for cross border fund transfers which involve moving funds through a complex web of multiple banks, domestic and international payment systems. Similarly, in the capital markets, for executing a trade, several intermediaries such as exchanges, central counterparties, central securities depositories, investment managers and more must update their respective databases with the transaction. The increased number of processing layers belonging to different organizations introduces delays and increases costs.
Blockchain’s fandom isn’t restricted to banking alone. It has admirers beyond the financial services – from real estate, precious metals and stones, to music and the wine industry – are discovering ways blockchain can lend ultimate transparency in tracking assets along their entire lifecycle.
The original blockchain, known as the underlying technology of the digital currency bitcoin, is also known as the bitcoin blockchain. (In this post, I’ll refer to it as simply the blockchain).
Blockchain, a sophisticated technology, uses advanced computer science and mathematics to encrypt, validate and record transactions. Transactions, once written, cannot be altered. Blockchain isn’t maintained by one entity. Instead it’s a distributed database that’s autonomously managed by an extensive network of private computers.
And this where the terrain quickly gets obfuscating – autonomously managed, network, private computers, distributed, unalterable records. Questions such as what do these terms mean, how are decisions made about recording transactions, can private computers be trusted to maintain data integrity? are natural!
Most blockchain related articles focus on it from the business perspective – the use cases, companies involved, projects initiated and so on. The hype around blockchain has given it mythical powers of a technology that can do just about anything. The technology, although undoubtedly a radical one, is still in its early days and is contingent on many factors such as interoperability, standardisation, and regulation. Its potential, capabilities and limitations are either being discovered or defined.
The focus of this post, the first in a series, is to simply understand as a business technologist, the basics of the blockchain and its underlying structure – what makes it the way it is.
To do so, we’ll take a quick look at the universe to which blockchain belongs.
Distributed Ledger Technology
The terms “distributed ledger technology” (DLT) and “blockchain” are often used interchangeably. Blockchain, in fact, is an example of a distributed ledger technology.
Other well-known examples of distributed ledger technology are Ethereum, Ripple, Multichain, Hyperledger and Everledger.
Distributed ledger technology is characterized by a shared, synchronized database that’s replicated throughout its network. DLT is an append-only database, which means transactions recorded in it are written just once and read any number of times.
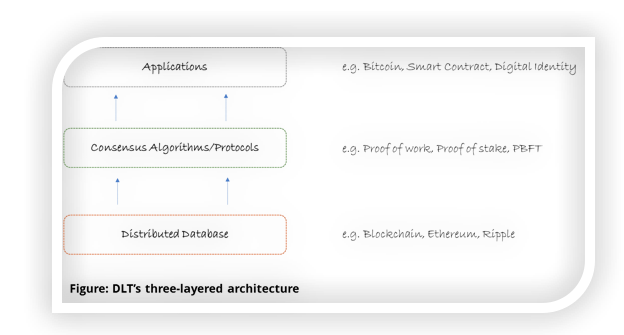
To achieve its synchronized state, DLT uses consensus protocols or algorithms to drive agreement amongst all or a select set of participating nodes in its network. (A node is nothing but a private computer connected to the internet and running the blockchain software).
The part about “all or select set of participating nodes” is what defines the two main types of DLTs –
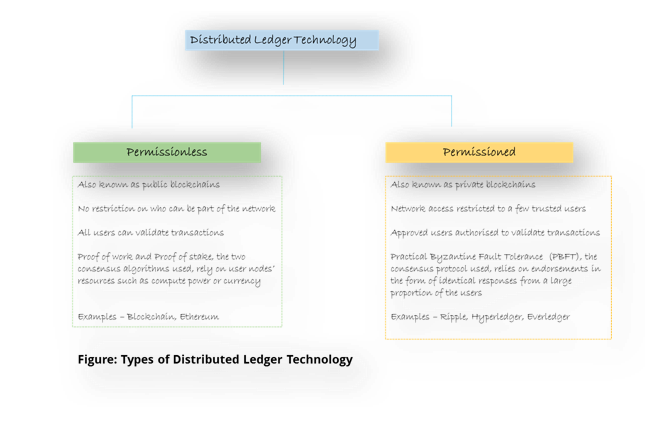 Because a distributed ledger is replicated across many entities, additional resiliency and data integrity are ensured. Even if any of the nodes in a network fails, the ledger remains intact due to the remaining nodes. What happens if all the nodes in a network fail at the same time? The chances of the vast number of nodes in a DLT (in case of blockchain it’s in millions) all failing at the same time, is negligible.
Because a distributed ledger is replicated across many entities, additional resiliency and data integrity are ensured. Even if any of the nodes in a network fails, the ledger remains intact due to the remaining nodes. What happens if all the nodes in a network fail at the same time? The chances of the vast number of nodes in a DLT (in case of blockchain it’s in millions) all failing at the same time, is negligible.
This is a major reason why DLT has strongly resonated with both the financial services and governance. To record a financial transaction, as seen in the cross-border payments or capital markets examples, large amount of data is duplicated across disparate systems belonging to the intermediary organisations. Lack of standardisation among these systems results in data inconsistency leading to costly reconciliation processes. DLTs, on the other hand, carry a single version of truth. Another advantage is that DLTs can bring down the costs of building an infrastructure that is not just shared but also trusted by entities that may not otherwise have reasons to trust one another, as in governance for instance.
Early this year, when government enforcement officials decided to investigate Uber for illegally operating in certain cities and countries, Uber found ways to not just identify but also evade such officers. The officers were shown false data about their upcoming rides along with incorrect information about the drivers, ensuring the officers couldn’t ride an actual Uber car and impose fines on the driver.
Late in 2015, Airbnb disclosed that 95% of its hosts have listed their property exactly once on its website. It was soon found out that just before the public announcement, Airbnb had purged its database of over 1,000 illegal apartment listings to avoid running afoul of New York city’s rental property laws.
Uber and Airbnb are companies that’ve defied conventions by ushering in the sharing economy, riding on the coattails of improved transparency. But as the above incidences show, even such venerable organizations are susceptible to misusing their rights as data owners, for short term gains.
And this is where a blockchain-like technology shows promise. But to understand, what makes a blockchain more secure, we’ll need to dive deeper into what constitutes a blockchain.
Building blocks of Blockchain
A blockchain is defined as a secure, distributed and shared database that stores transactions.
Let’s try to deconstruct the above definition to identify the building blocks of a blockchain –
- Transactions
- Shared
- Distributed
- Shared
Transactions
It all starts with a transaction. A transaction could be something as simple as a payment or fund transfer. Or it can represent assets such as property titles, precious commodities, votes, music rights, customer details and more – all encapsulated in a digital form.
Shared
Normally, a transaction for fund transfer or payments would be verified and approved by your bank, with the transaction recorded in the bank’s central server.
But in a blockchain set-up, when a transaction is transmitted to the entire peer to peer network, each node in the network will receive the transaction, update its copy of the database with the latest transaction before sharing it with the rest of the nodes in the network.
Distributed
Because there is no one single entity that is entrusted with storing a transaction centrally, transactions are captured in a distributed file, stored and maintained by the network – basically, the same copy of the blockchain is duplicated and stored on each node in the network, with each node holding the same, most-current version of the database.
Secure
In the event where multiple transactions are requested and cancelled at the same time, how does blockchain operate? Which transaction happened first and which one is the latter can become a tough puzzle to solve given there’s no central arbitrator.
Who defines what is ‘latest’ on a blockchain?
Making of a block
It’s the nodes that must agree about the order in which transactions are received and added to the blockchain.
Rather than updating single transactions, nodes in the network club together many such transactions into groups called blocks.
The transactions that get added to a block therefore, can originate from several different requests that would have occurred at about the same time. A block can accommodate a finite number of transactions and a typical block size is around 1 MB – capped to avoid network congestion. A block is added to the blockchain every 10 minutes.
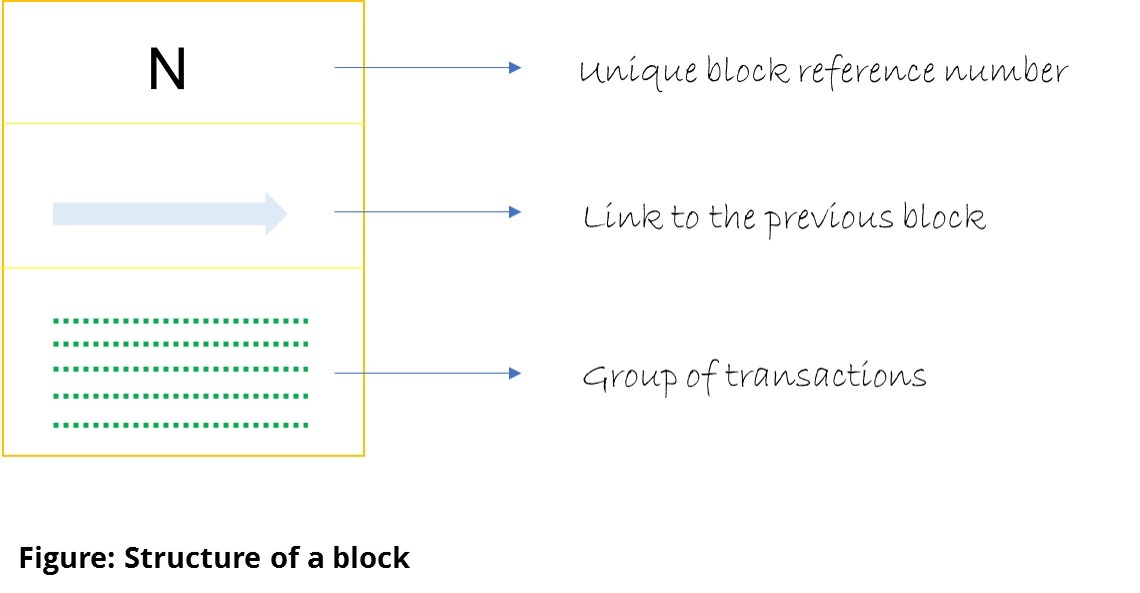
What’s in a name?
Because transactions in a block are considered to have occurred at the same time, the time-stamped nature of each block along with references to the previous blocks help chronologically sequence the block in a chain of blocks – hence the name blockchain.
Building consensus
Given the distributed and decentralized nature of the network, where any node can ‘author’ a block by lumping together transactions into a block and attempting to transmit it to as the next block on the network, there can be utter chaos. With millions of autonomous nodes, how is the security of the blocks ensured?
To answer this question, we’ll lightly skim the world of digital signatures and cryptographic functions.
Remember one of the attributes of distributed ledgers is that all nodes must agree on the correct state of a shared data source. DLT employs consensus algorithms to validate and agree that the data being added is the same throughout the network. There are two main types of consensus algorithms used by permissionless blockchains – proof of work and proof of stake. Proof of work is the consensus protocol used by blockchain whereas proof of stake is an upcoming protocol, one proposed by Ethereum blockchain. In a later post, we’ll look at the difference between these two algorithms in greater detail. Outlined here is how proof-of-work works to secure the blockchain.
Proof of work algorithm is executed more like a competition – the nodes compete by proving they have used up a certain amount of computing power to solve a mathematical problem and validate a block.

With so many nodes in a network, ensuring security of the transactions and thereby, blocks become paramount. To do so, blockchain employs advanced encryption technology such as cryptographic hash functions to encrypt blocks. In a peer to peer network, the threat of malicious actors who’ll attempt to subvert the system by spamming the network with false messages resulting in a ‘denial of service’ is just as real as it’s in a conventional network. Cryptographic hash function is a secure and robust method to verify integrity of the blocks.

Because a hash value is sensitive to change, if someone tries to change it on the blockchain, everyone on the network will know it. Cryptographic hash function therefore, ensures the blockchain records are tamper proof and secure.
A consensus protocol such as proof of work uses cryptographic hash function to ensure not only the legitimacy of the blocks that get added to the network but also the rigour of the process by which the mathematical puzzle is solved and the blocks’ validity ascertained.
Proof of work – all about random integers, network target and cryptography
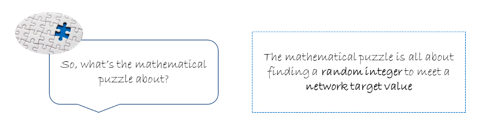 Random integer
Random integer

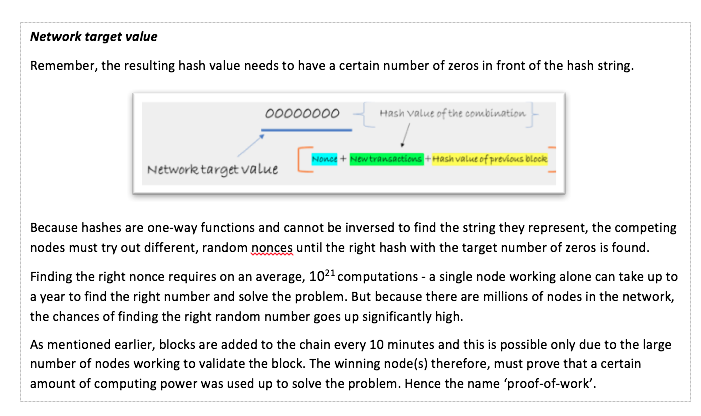
In a situation where two or more nodes simultaneously solve the mathematical problem, the blocks are broadcast to the network by the respective winning nodes. The other nodes in the network add the winning node that they each receive to the longest chain. This helps resolve the ambiguity of which block would be considered valid since all the nodes adopt the longest chain as the final state of the blockchain.
Consensus protocols – The Litmus Test
Proof of work is a rather complex way of achieving consensus amongst disparate entities. Not only does it require significant amount of computing resources but also impacts the system throughput due to the latency in validating and adding the blocks.
How do the other consensus protocols stack up against proof of work? What are the upsides and downsides to using those? Answers to these questions are important, given the critical role that consensus protocols play in determining the type of blockchain best suited for a business use case.
References
Article by channel:
Everything you need to know about Digital Transformation
The best articles, news and events direct to your inbox
Read more articles tagged: Blockchain, Featured







