I was happily ignorant about information risk , until very recently – when I got a gun at my head – I was hired by a company who is a leader in information risk management solutions to head their marketing (#Aujas). The good things aside – I lost all my excuses to continue to be in my safe bubble and blissfully assume everything is fine as long as my #antivirus was showing green ! 😉
I have been talking with a lot of people – customers, practitioners & security experts in the last few days and the experience has been very valuable and exciting at the same time – Now I am less ignorant – no longer the ostrich with its head inside the sand ! LOL (#infosec)
This topic is very relevant given that there is a raging debate about data privacy vs. national security between Apple and FBI (#unlockiPhone, #AppleVsFBI). I was plainly amazed by the fact that Apple created a strong anti-hack with 2 simple checks. Loved it ! I shall not digress from my original topic by getting into the debate here. All I want to say is that information risk and security is no longer an operations/IT topic, it has a significant impact on the company’s business from a strategy perspective. As a senior leadership/C-level – this is important for you, irrespective of your functional focus or compliance needs.
What I realized is that data security is not an easy area. Everyone knows it is important, but it is very vast and complex, and the threat landscape keeps changing, making it very challenging to get a proper foothold.
I thought I should summarize my learning’s to help others like me do a quick ramp up. So here we go.
I am dividing this into 2 sections. The Problem and The Solution.
(Btw, when I say hacking here – I am always referring to the “unethical” kind. i.e the bad kind.)
Part I – Why you need to worry about information risk ? (The Problem)
1. Information is the MVA (Most Valuable Asset)
In today’s world – It is very hard to argue that there is anything more valuable than “information” for any organization. Data is your biggest asset, no matter what business you are in. You might be a manufacturing company, yet the data in your systems is valuable, maybe even more valuable than the gigantic machines in your factory !
Nothing can reinforce this better than the hard facts below.

Source: Tom Goodwin in TechCrunch.
Even if you discount the value of the business model from the equation, you can still safely say that non-physical assets are very valuable.
2. Data Breach is Very Common
As long as you have data in your device(s) and it is connected to the internet – you are at the risk of someone breaking-in and stealing that data.
Data breach incidents are very common. Sony, Ashley Madison, Snapchat, etc are just the tip of the iceberg. We see some of it in the news, but a lot of it is not know publicly. It also reflects in the in the survey done by Pwc – respondents said only 33% of the incidents slipped into public domain. The majority was know internal only.
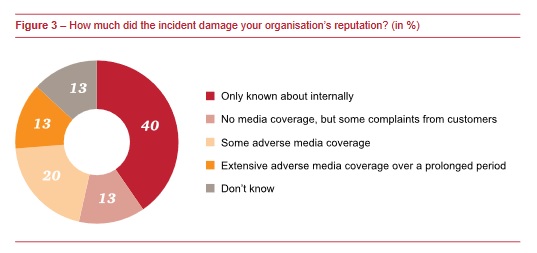
Source: Information Security Breaches Survey by Pwc Belgium, Jan 2015
You might be asking yourself – what is the use of my data to someone else ? probably no use whatsoever ? wrong ! The question to ask is – “what is the value of that data to you ?” and this changes the whole paradigm of risk.
One of the simple tricks these days is for someone to get access to your device and “encrypt” the data – then ask for money to “decrypt” it back. Simple yet very powerful tactic. A good analogy would be what if the thief replaced the lock to your safe at home with his own lock and asked for money to give you the new key ? If you don’t pay – he might not gain anything, but you have a lot to lose ! Of-course, depends on what you have in that safe. And people are smart enough to target the right prey !! 😉
Now imagine the size of this risk if yours is a company with many people, using many devices, storing a lot of important data… and continuously connected to the internet. Strangers can walk in through one of the many doors, and walk out without you even having the slightest clue. Very Scary !!
3. Many (Unknown) Enemies
Vested agents are of 4 kinds -Criminals, Competitors, Employees & Activists. the motivations are different, but the means are the same.
Criminals – As the name says – they are looking to make big money with low calculated risks.
Competitors – typically want to get a sneak peek into your secret plans.
Employees – might be disgruntled employees trying to get even Or joining a competitor and wants to carry old work copies to impress the new boss 🙂
Activists – Fighting for a cause – good or bad. typically not interested in making money, but want to make a point.
So basically there are a lot of people both externally, and internally who can find good use of your data. And we did not even talk about cyber espionage here – the state sponsored kinds !
4. Cyber-crime is a Lucrative Business
It is a myth that cyber crime needs high-end sophistication and technology. Don’t get carried away by Ocean’s 11 kind of movies where the bad guys are as sophisticated as George Clooney and Brad Pitt (looks-wise at-least as per my wife!).
It can be done with pretty low tech tools. There is also hacking-as-a-service with offerings starting as low as a few $100’s. So firstly – it is a low investment business. and secondly – the risk of getting caught is very low given the cyber laws in many countries and the international jurisdiction – since most of these attacks happen from places of safe haven outside of your home country.
Low entry barriers plus low risk of getting penalized, along with high upside opportunity makes cyber crime one of the most lucrative industries…. probably even better than drug cartels ?
5. Brand Image at Risk ?
“Annual cost to the global economy from cyber crime is $400+ billion”
Source: Center for Strategic and International Studies (CSIS) & Mcafee, June 2014
Given that the reported financial loss due to data breach is just in $100’s of Millions, but the total cost is in $100’s of Billions. The difference is a mind boggling 1,000 x ! This clearly indicates that the risk is much much larger than just the financial loss.
Therefore it is also not surprising that many security experts encourage companies to pay “ransom” in such situations. Because it is a cheaper option clearly. (Does not guarantee that you will not have a repeat attack though. )
Information security is all about risk mitigation and building trust that the company’s most valued assets are safe. In that sense it is very similar to the financials of the company, which is all about risk mitigation and trust building in the long-term sustenance of the company as a viable business.
Part II – What can you do about information security ? (The Solution) “everybody is vulnerable” is a fact, similarly “nobody is 100% secure” is also a fact.
The good news is that there are a lot of things you can do, and there are systems, tools & services available to keep your assets safe and secure. Here lets look at the top areas to pay attention.
6. People are your Weakest Link
It is kind of obvious, but worth emphasizing that we people are the weakest link in the security armor. Also it is not just current employees – it can be past employees, service providers, suppliers & even partners.
If we look at the data breach incident report put together by DBIR – the top 4 categories account for 90% of the incidents. And they are all people related – whether it is goofing up, getting infected, behaving badly or just losing stuff.
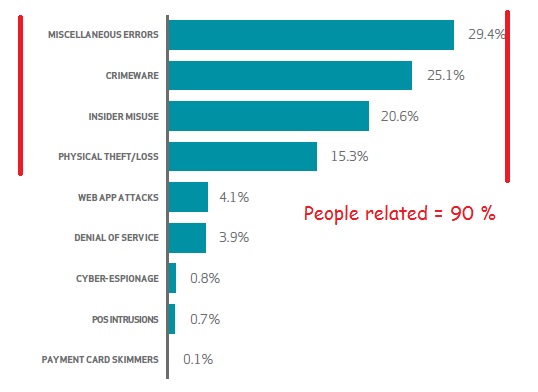
Source: 2015 Data Breach Investigations Report (DBIR)
There are 3 areas where you need to pay attention from a security perspective –
Access Control – Who has access to what data ? Does not make sense for people not related to have access to sensitive data. Also you need to have a fool proof way of authentication, especially with things like single sign-on across multiple applications/devices.
Data Leakages – One of the prominent ways data gets stolen is by employees sending confidential data to outside-company/unsecure channels – knowingly or unknowingly.
Social Engineering – commonly called Phishing. It is a tactic where the bad guys use human psychology and weakness to make you do things that you never would do in your sane mind. E.g. Share bank account/credit card details with thieves, fall for greedy scams – “rich lady in Timbuktu wants to give away her fortune to you because she does not trust anyone in her country”, “Coca Cola wants to give you a few millions just for reading this email”, “you’ve won a million$ lottery and have to pay a small fees of few thousands to claim it”, etc, etc. Looks familiar ? It can sometimes be more sinister like making you reveal your banking credentials, or something sly like installing a software in your computer that continuously steals data and sends it outside, and you don’t even get to know.
This is where training people and making everyone aware of common threats and implications will help immensely.
7. Protect (Important) Data
There are attackers, but also a good % of the breaches are due to inadvertent errors – systems or people related. It is a highly recommended practice to protect data by putting systems and processes in place for storing and backing-up.
Every piece of data is valuable. But some data is more valuable than others. Typically financial, customer & employee data is valuable to everyone, but there can also be specific data as per the industry. example – new designs in automotive, vendors data in supply chain, source code in software, etc etc.
Typically it will be a small % of the overall data volumes and it is quicker and cost-effective to just segregate this high risk data from the rest of it and put the right security measures.
8. What does your (Security) Data say ?
A big win in the case of many critical illnesses today is that – they start showing signs in advance of time, and you can manage it a lot better if you pay attention to the early signs. Same applies to information security. Looking at the available data and monitoring what is happening across all the entry points gives a ton of insights into past attacks and future vulnerabilities.
“59% of the companies said they leverage big data”
Source: Global state of information security survey by Pwc, Jan 2016
The average time taken for the company to know that there has been a security breach is 6 months !! And in most cases the breach is reported by external agencies first. Very bad from an reaction-action perspective. The quicker you get to know – the better, because you can assess the damage and can take damage control measures in terms of remediation and PR management.
“48% of the companies said they actively monitor and analyze intelligence”
Source: Global state of information security survey by Pwc, Jan 2016
With intelligence – you can even predict attacks, because it is very similar to conquering strong forts. Smart enemies will not do an ambush on the fort without doing some kind of small attacks to test the vulnerabilities ?
9. Connected Devices come with a (Security) Cost
Internet of Things (IoT) has taken the consumer experience to the next level of excitement. Home automation, Medical devices, Smart cities, Fitness devices, Automobiles, so on and so forth – the uses are many, and it is expanding rapidly. This typically involves devices (or components) that are always connected to the internet, which means they are easy targets for security breaches.
As expected – the security incidents on connected devices have multiplied in the last year as seen below in the Pwc survey.
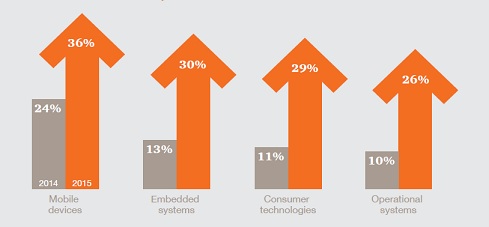
Source: Global state of information security survey by Pwc, Jan 2016
Therefore you need to pay special attention to data security when you are dealing with connected devices – especially upstream in the design stage when the costs are really low. Because just like software bugs – the cost of security snowballs as it moves downstream into the hands of consumers.
10. Cyber Insurance can be of help
You can take an insurance to cover the risk of information security. As the saying goes “what cannot be protected can be insured”.
Below you can see the popularity of cyber insurance across the enterprise sizes. Of-course it is not surprising to see that the bigger companies have higher penetration, but it is interesting to see how the smaller ones are open to the idea of insurance.
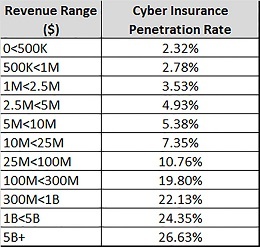
Source: Cyber Risk Network by Advisen, Jan 2015
But the problem is this – there is a general inability to forecast security risk making it difficult for companies to benchmark their relative risk to their peers. This makes it difficult for insurance companies to develop actuarial data to calculate premiums and to determine the relative risk profile of the companies they insure.
Therefore the coverage and premiums are primarily dependent on the security controls you already have in place. A space definitely worth watching.
11. Test It – Stay on top of Threats
Testing your security infrastructure with live assessments is a good way of knowing the vulnerabilities and future risk potential. You can do a black-box test (live system) or a white-box test (source code) and everything in-between as the shades of grey !
“49% of companies said they conduct threat assessments”
Source: The global State of Information Survey by Pwc, Jan 2016
It is also highly recommended to do regular audits to understand the sate-of-security of your enterprise in the context of the ever changing threat landscape.
Summary :
As a CXO – it is important to pay attention to the state of security of your digital assets because data is super valuable and it is always at risk of getting breached. Security is not as complicated as it sounds to be. It is usually the simple basic things that is responsible for the majority of the issues.
Now over to you for hearing from your experiences ….
Liked It ? Please Share It !
———————————————————————————-
About Author – I am Anupam Bonanthaya and I am interested in topics on information security, marketing and people. I am also the Chief Marketing Officer at Aujas.
Aujas (www.aujas.com) is an IDC invested company specialized in the Information Risk Management services and solutions – We are securing 1billion+ identities globally, and working with 390+ customers across 22 countries. If you want to talk to one of our (200+ certified) security experts – give us a shout – click here !
You can write to me at anupam.bonanthaya@aujas.com, and connect with me on LinkedIn
—————————————————————————————
Article by channel:
Everything you need to know about Digital Transformation
The best articles, news and events direct to your inbox
Read more articles tagged: Featured, Hacking, Ransomware